Blogs
DON’T BE THE NEXT VICTIM OF A CYBER ATTACK
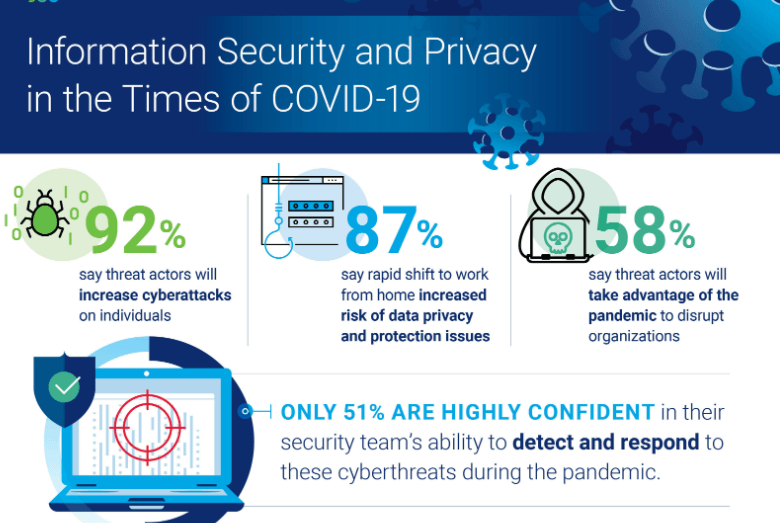
Cyber-attacks are demolishing businesses more than COVID-19 is. Don’t trust us? See these two stats (there are tons of other stats): Up to 88% of UK companies have suffered cyber-attacks in the last 12 months (Source) One small business in the UK is successfully hacked every 19 seconds. (Source) And this isn’t even the worst news. The […]
Unlocking New Possibilities: How Trevonix Can Help Boost Competition in the UK’s Future of Payments.
Open banking standardizes the format and requirement for banks to open their data to third parties. This has revolutionized the financial industry, giving consumers more control over their own financial data and facilitating the development of new innovative services. Trevonix, offers advisory & implementation services that enable businesses to leverage open banking to boost competition […]
Navigating the Merger: Ping Identity and ForgeRock
Introduction: In the ever-evolving landscape of digital identity and security, the recent merger between Ping Identity and ForgeRock has sent ripples through the industry. Both companies have long been stalwarts in the Identity and Access Management (IAM) space, each with a rich history of providing robust solutions to enterprises worldwide. As the dust settles on […]
Protecting Against Social Engineering
In 1995 the arrest of Kevin Mitnik signaled to companies around the world that privileged access could be obtained by a simple phone call. Fast forward over 28 years and we have news of several Las Vegas Casinos still falling victim to Social Engineering exploitation. Don’t you think now is a great time to ensure […]
Governance (IGA) over Employee and Customer user identities
On the subject of SaaS Identity Governance… Identity Governance & Administration (IGA) over Employee & Customer user identities is a non-stop task for organizations today. In years past, IGA teams struggled with different tool sets that were created at a time when “SaaS” was a dirty 4-letter word. Their IAM counterparts, however, were able to […]
Understanding Okta IGA: Identity Governance and Administration
Introduction In today’s digital era, identity management is crucial for organizations of all sizes. Managing user access, entitlements, and security is not only a compliance requirement but also essential for protecting sensitive assets and maintaining operational efficiency. Okta Identity Governance and Administration (IGA) is a comprehensive solution designed to streamline IAM processes while ensuring compliance. […]
Exploring the Power of Okta Device Access
Exploring the Power of Okta Device Access In today’s ever growing digital landscape, securing access to sensitive data and applications is critical. As organizations embrace remote work, cloud-based solutions, and mobile devices, the need for robust identity management has never been more crucial.In this blog, we will investigate the new capabilities of Okta’s Device Access […]
Why IAM is the first challenge to implement Zero Trust
Why IAM is the first challenge to implement Zero Trust Zero Trust is the most common buzzword in the Cyber Security currently, but we have got feedback from many customers asking how to go about achieving it. In this article, we explain why Identity and Access Management is central to implementing Zero Trust. The Zero […]
Modernizing your IAM stack this year? There is still time!
Historically, IAM architecture is the last to modernize within a company. Front end, API versions, legacy data stores, etc… Everything changes before the identity authentication and authorization. When companies host their own IAM infrastructure it typically involves many different teams dealing with topics like know your customer (KYC), registration, app and network admins, DB admins, […]
Multibrand Customization
Objectives: Understand what is multi-brand customization and where it can be used. Use Case: A company called “XYZ Corporation” manages three different products. Each product has its own website, applications, and user base. However, the company wants to provide a unified login experience across all three products by using Okta. By leveraging Okta’s multi-brand customization […]
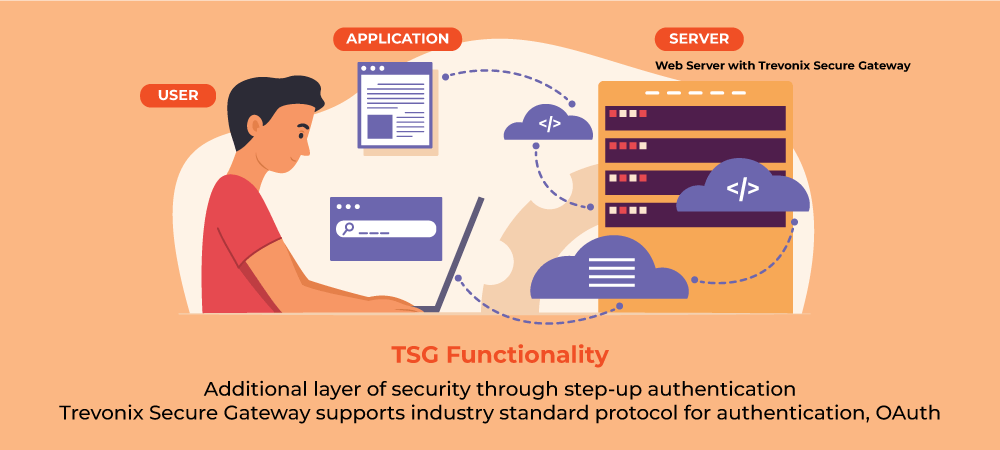
Securing Legacy Applications Made Easy with Trevonix Secure Gateway
Introduction As technology evolves, many companies find themselves with legacy applications that may have become vulnerable to security threats due to outdated code or lack of regular updates. However, securing these legacy applications can be challenging, as modifying the code can be time-consuming, risky, and costly. That’s where Trevonix Secure Gateway comes in – a powerful tool/module developed by our company […]
Unlocking New Possibilities: How Trevonix Can Help Boost Competition in the UK’s Future of Payments.
Open banking standardizes the format and requirement for banks to open their data to third parties. This has revolutionized the …
Navigating the Merger: Ping Identity and ForgeRock
Introduction: In the ever-evolving landscape of digital identity and security, the recent merger between Ping Identity and ForgeRock has sent …
Protecting Against Social Engineering
In 1995 the arrest of Kevin Mitnik signaled to companies around the world that privileged access could be obtained by …
Governance (IGA) over Employee and Customer user identities
On the subject of SaaS Identity Governance… Identity Governance & Administration (IGA) over Employee & Customer user identities is a …
Understanding Okta IGA: Identity Governance and Administration
Introduction In today’s digital era, identity management is crucial for organizations of all sizes. Managing user access, entitlements, and security …
Exploring the Power of Okta Device Access
Exploring the Power of Okta Device Access In today’s ever growing digital landscape, securing access to sensitive data and applications …