
Why IAM is the first challenge to implement Zero Trust
Zero Trust is the most common buzzword in the Cyber Security currently, but we have got feedback from many customers asking how to go about achieving it. In this article, we explain why Identity and Access Management is central to implementing Zero Trust.
The Zero Trust framework follows a “never trust, always verify” policy. It doesn’t distinguish between internal and external users or devices; it treats everything as external. User is the crucial aspect for the Zero Trust concept.
Traditional security approaches were designed to protect the organization’s perimeter. However, in the current world of Cloud-based services, SaaS and hybrid working, the boundaries of what is internal and external is more blurred than ever. The assumption to trust things within an organization’s network can be trusted no longer holds true.
What is Zero Trust
As per the NIST (NIST SP 800-207: Zero Trust Architecture 2020), Zero Trust provides a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised.
Zero Trust Maturity Model
The Zero Trust Maturity Model (CISA – https://www.cisa.gov/sites/default/files/2023-04/zero_trust_maturity_model_v2_508.pdf )represents a gradient of implementation across five distinct pillars, where minor advancements can be made over time toward optimization. The pillars include Identity, Device, Network, Application Workload, and Data. Each pillar also includes general details regarding Visibility and Analytics, Automation and Orchestration, and Governance. This maturity model is one of many paths to support the transition to zero trust.
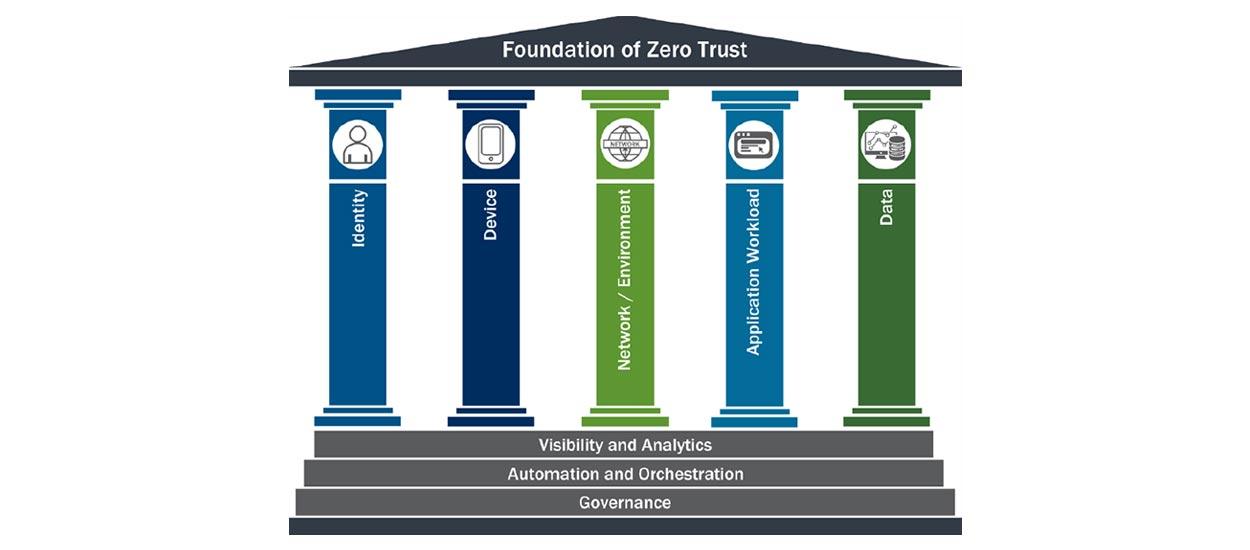
As one of the fundamental pillars for Zero Trust, Identity plays a crucial role in achieving Zero Trust Architecture and holds key to implementing it successfully. Forrester (who coined the term Zero Trust) https://www.forrester.com/blogs/ombs-zero-trust-strategy-government-gets-good/, describes IAM as the first Pillar while implementing Zero Trust roadmap.
At Trevonix, we have put a checklist for Identity and Access Management implementation towards achieving Zero Trust. If you need more information or guidance, please reach out to info@trevonix.com where our experts will work with you to solve the challenges you and your organisation are facing.
Checklist for implementing IAM for Zero Trust
Zero Trust is the most common buzzword in the Cyber Security currently, but we have got feedback from many customers asking how to go about achieving it. In this article, we explain why Identity and Access Management is central to implementing Zero Trust.
The Zero Trust framework follows a “never trust, always verify” policy. It doesn’t distinguish between internal and external users or devices; it treats everything as external. User is the crucial aspect for the Zero Trust concept.
Traditional security approaches were designed to protect the organization’s perimeter. However, in the current world of Cloud-based services, SaaS and hybrid working, the boundaries of what is internal and external is more blurred than ever. The assumption to trust things within an organization’s network can be trusted no longer holds true.
