Protecting Against Social Engineering

In 1995 the arrest of Kevin Mitnik signaled to companies around the world that privileged access could be obtained by a simple phone call. Fast forward over 28 years and we have news of several Las Vegas Casinos still falling victim to Social Engineering exploitation. Don’t you think now is a great time to ensure […]
Multibrand Customization
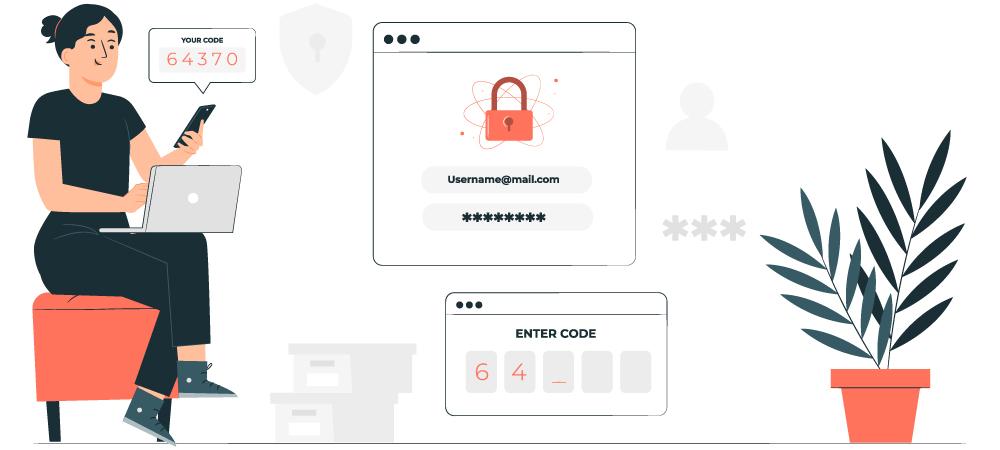
Objectives: Understand what is multi-brand customization and where it can be used. Use Case: A company called “XYZ Corporation” manages three different products. Each product has its own website, applications, and user base. However, the company wants to provide a unified login experience across all three products by using Okta. By leveraging Okta’s multi-brand customization […]
Securing Legacy Applications Made Easy with Trevonix Secure Gateway
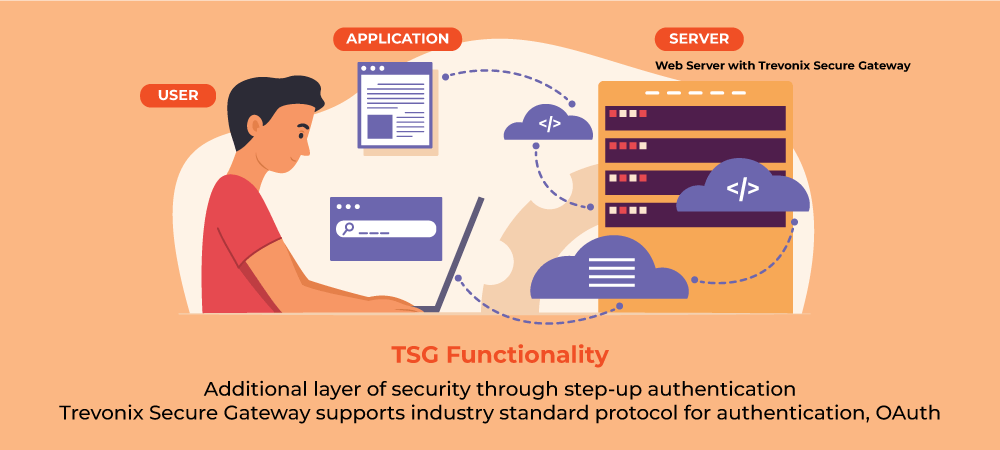
Introduction As technology evolves, many companies find themselves with legacy applications that may have become vulnerable to security threats due to outdated code or lack of regular updates. However, securing these legacy applications can be challenging, as modifying the code can be time-consuming, risky, and costly. That’s where Trevonix Secure Gateway comes in – a powerful tool/module developed by our company […]
Office 365 integration with PingFederate
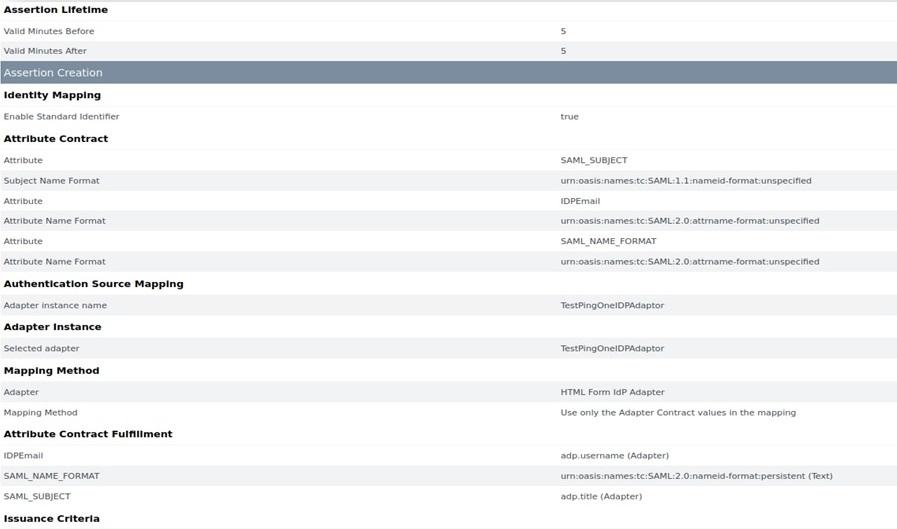
Introduction Office 365 is Microsoft’s cloud-based Office solution. Out of two variants of Office 365 that Microsoft offers (desktop option, where users have Office applications (e.g.: Word, etc) installed locally on desktops, but documents and files are stored in the cloud; and a web client, where both documents and applications are stored in the Cloud. […]