Blogs
DON’T BE THE NEXT VICTIM OF A CYBER ATTACK
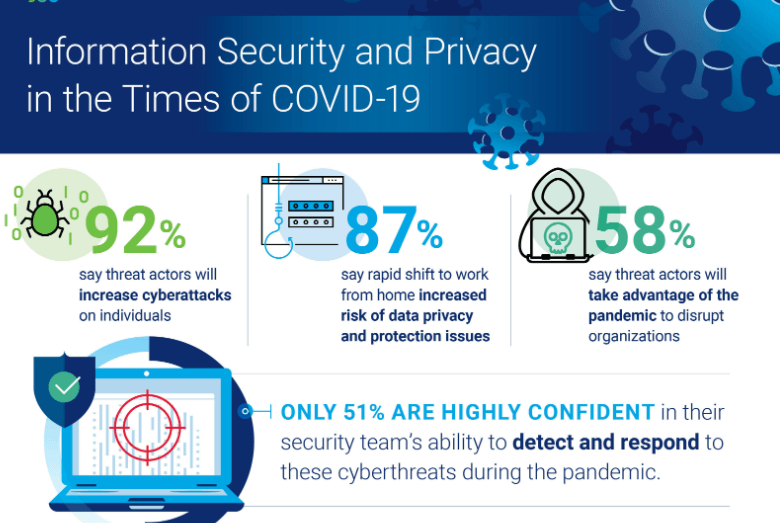
Cyber-attacks are demolishing businesses more than COVID-19 is. Don’t trust us? See these two stats (there are tons of other stats): Up to 88% of UK companies have suffered cyber-attacks in the last 12 months (Source) One small business in the UK is successfully hacked every 19 seconds. (Source) And this isn’t even the worst news. The […]
What is IAM Automation? Benefits, Challenges, and Tools
In today’s fast-paced digital world, managing who can access what within an organization is more important than ever. Identity and Access Management (IAM) is the foundation of cybersecurity strategies for businesses across all industries. IAM ensures that the right individuals have the right access to the right resources at the right time. However, with the […]
What is Application Security | Types, Tools & Best Practices
In today’s highly connected digital world, the safety of applications has become more important than ever before. Cyber threats are on the rise, targeting software systems across industries. Application security plays a key role in preventing unauthorized access, data breaches, and cyberattacks. By applying the right techniques and tools, businesses can ensure their applications are […]
What is Zero Trust Security Model? A Complete Guide
In today’s world, cybersecurity is more important than ever. With cyber-attacks becoming more frequent and sophisticated, businesses and individuals need stronger protection. One popular approach that many organizations are now adopting is the Zero Trust Security Model. In simple words, the Zero Trust Security Model means “never trust, always verify.” Instead of trusting anyone inside […]
10 Key Factors to Consider When Choosing a PAM Solution in 2025
In today’s ever-evolving digital landscape, securing sensitive information has become more critical than ever. Organizations across industries are increasingly targeted by cybercriminals aiming to exploit privileged accounts. This is where privileged access management solutions play a crucial role. PAM solutions are designed to protect an organization’s most critical assets by controlling, monitoring, and securing privileged […]
What is Data Protection and Why is it Important? A Complete Guide
In this blog, you will learn what data protection is, why it matters, the key principles behind it, and the best practices to follow. We will also explore the difference between data protection, data privacy, and data security, as well as the challenges and technologies involved. By the end of this guide, you will understand […]
What is a Risk Assessment? A Complete Guide
In this blog, you will learn everything you need to know about risk assessment—from its basic definition to its role in the risk management process. We’ll explore examples from different industries, explain how to use a risk assessment matrix, and introduce popular risk analysis tools. We will also share the best risk assessment software options […]
What is Identity Security?
In this blog, you’ll learn everything you need to know about identity security. We’ll explore what identity security is, why it’s important, how it works, and the tools used to protect digital identities. From the key components to future trends, you’ll understand how identity security plays a critical role in defending against modern cyber threats. […]
What is PAM? A Guide to Privileged Access Management
In this blog, we will explore Privileged Access Management (PAM), its importance, key features, benefits, and best practices. We will also discuss different types of privileged accounts, the risks associated with them, and how PAM helps organizations secure their sensitive data. By the end of this guide, you will have a clear understanding of PAM, […]
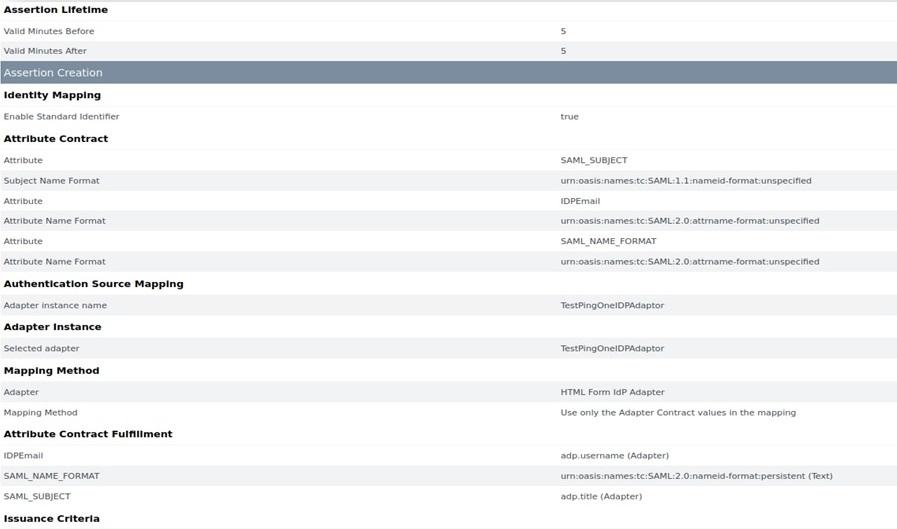
Office 365 integration with PingFederate
Introduction Office 365 is Microsoft’s cloud-based Office solution. Out of two variants of Office 365 that Microsoft offers (desktop option, where users have Office applications (e.g.: Word, etc) installed locally on desktops, but documents and files are stored in the cloud; and a web client, where both documents and applications are stored in the Cloud. […]
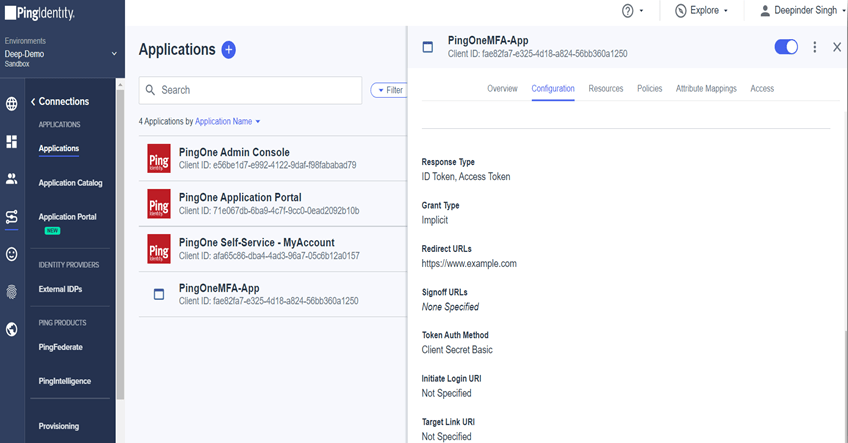
PingOne MFA integration with PingFederate
Introduction One of security challenges is to verify that a user requesting access to a protected resource is who they claim to be and that they are permitted to access the requested resource. MFA is a process that uses two or more factors to verify an identity. These factors are:- Knowledge (username/password, PIN, etc), Possession […]
What is IAM Automation? Benefits, Challenges, and Tools
In today’s fast-paced digital world, managing who can access what within an organization is more important than ever. Identity and …
What is Application Security | Types, Tools & Best Practices
In today’s highly connected digital world, the safety of applications has become more important than ever before. Cyber threats are …
What is Zero Trust Security Model? A Complete Guide
In today’s world, cybersecurity is more important than ever. With cyber-attacks becoming more frequent and sophisticated, businesses and individuals need …
10 Key Factors to Consider When Choosing a PAM Solution in 2025
In today’s ever-evolving digital landscape, securing sensitive information has become more critical than ever. Organizations across industries are increasingly targeted …
What is Data Protection and Why is it Important? A Complete Guide
In this blog, you will learn what data protection is, why it matters, the key principles behind it, and the …
What is a Risk Assessment? A Complete Guide
In this blog, you will learn everything you need to know about risk assessment—from its basic definition to its role …