Unraveling the Future: The Promise of Decentralized Identity

Introduction: In the dynamic landscape of digital innovation, few concepts carry as much transformative potential as decentralized identity. As we march into the heart of the 21st century, the paradigm of identity management is undergoing a profound shift, propelled by blockchain technology and a growing demand for privacy, security, and user control. Welcome to the […]
Embracing the Future of Authentication: Adopting Passkeys for Enhanced Security
Introduction: In the ever-evolving landscape of cybersecurity, traditional passwords are increasingly proving to be a weak link. The rise in cyber threats and data breaches has necessitated a more secure and user-friendly authentication method. Enter passkeys—a revolutionary step towards a safer digital future. At Trevonix, we are committed to guiding organizations through the adoption of […]
PingOne MFA integration with PingFederate
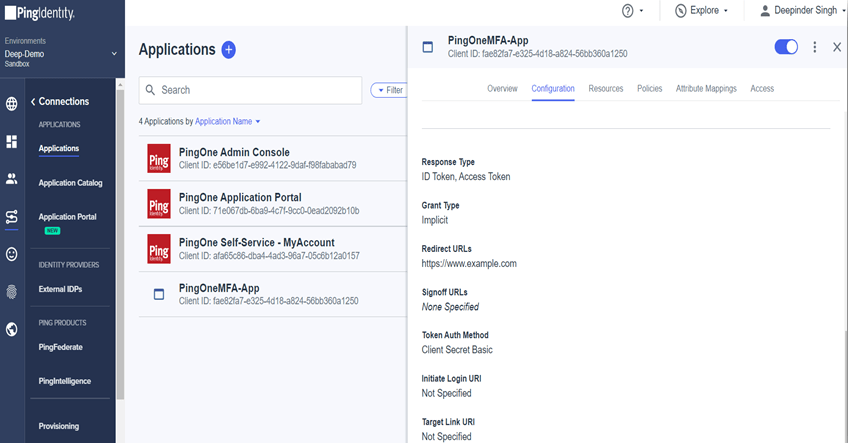
Introduction One of security challenges is to verify that a user requesting access to a protected resource is who they claim to be and that they are permitted to access the requested resource. MFA is a process that uses two or more factors to verify an identity. These factors are:- Knowledge (username/password, PIN, etc), Possession […]
Office 365 integration with PingFederate
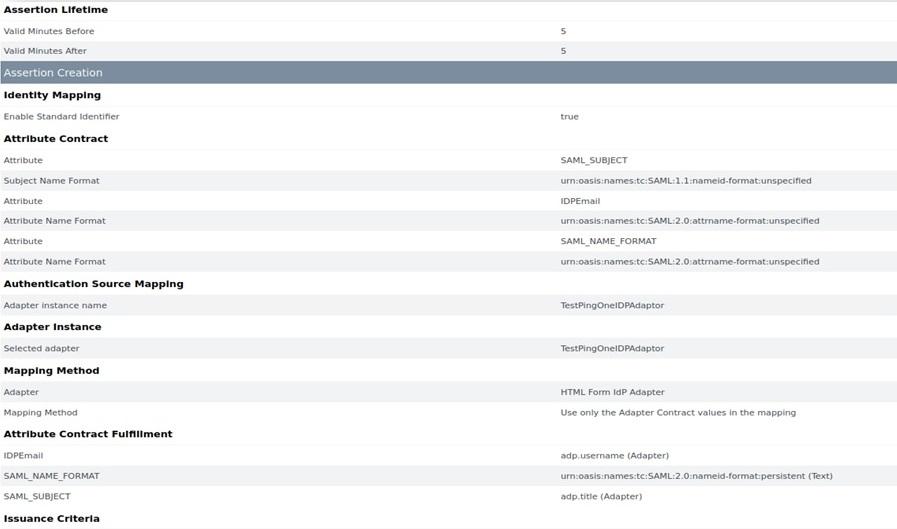
Introduction Office 365 is Microsoft’s cloud-based Office solution. Out of two variants of Office 365 that Microsoft offers (desktop option, where users have Office applications (e.g.: Word, etc) installed locally on desktops, but documents and files are stored in the cloud; and a web client, where both documents and applications are stored in the Cloud. […]
DASHBOARD FOR PINGFEDERATE INTEGRATED APPLICATIONS

PingFederate is an enterprise federation server that enables user authentication and single sign-on. It serves as a global authentication authority that allows employees, customers and partners to securely access all the applications they need from any device. PingFederate easily integrates with applications across the enterprise, third-party authentication sources, diverse user directories and existing IAM systems. […]