Introduction
Office 365 is Microsoft’s cloud-based Office solution. Out of two variants of Office 365 that Microsoft offers (desktop option, where users have Office applications (e.g.: Word, etc) installed locally on desktops, but documents and files are stored in the cloud; and a web client, where both documents and applications are stored in the Cloud.
SSO using PingFederate to O365 can be accomplished multiple ways: PingFederate with SAML, PingFederate with WS-Federation/WS-Trust, or an O365 SaaS Connector. In this below exercise, we will use SAML 2.0.
Objectives
- Configure O365 SP connection in PingFederate
- Configure O365 federation setting to authentication with PingFederate
Good to Know
- SAML 2.0 Authentication Protocol
- Authentication flows: IDP initiated (via PingFederate URL) SP initiated (Office 365 URL)
Pre-Requisite
- Office 365 should have a valid, non-default domain and is populated with a test user in it
- Validate that domain has authentication marked as ‘managed’.
- Admin must have administrative access to PingFederate and Office 365
- Install the Microsoft Azure Active Directory Module for Windows PowerShell
- Configure data store and PCV in PingFederate to authenticate the users requiring Office 365 application access
- Specify the SAML 2.0 IDP EntityID in the PingFederate>Systems>Server>Protocol Settings
- Validate if AzureAD user has immutableID set, if not set immutableID attribute for the user using below command, as this is required attribute for the federation to work
-
Set-MsolUser -UserPrincipalName "
" -ImmutableId $value
Steps to follow at PingFederate
Create a PingFederate SP connection for Office 365:
- Download the Office 365 SAML metadata from https://nexus.microsoftonlinep.com/federationmetadata/saml20/federationmetadata.xml
- Configure using Browser SSO profile SAML 2.0.
- Import the metadata from the downloaded Office 365 metadata file.
- Enable the following SAML Profiles:
- IdP-Initiated SSO
- SP-Initiated SSO
- SP Initiated SLO
-
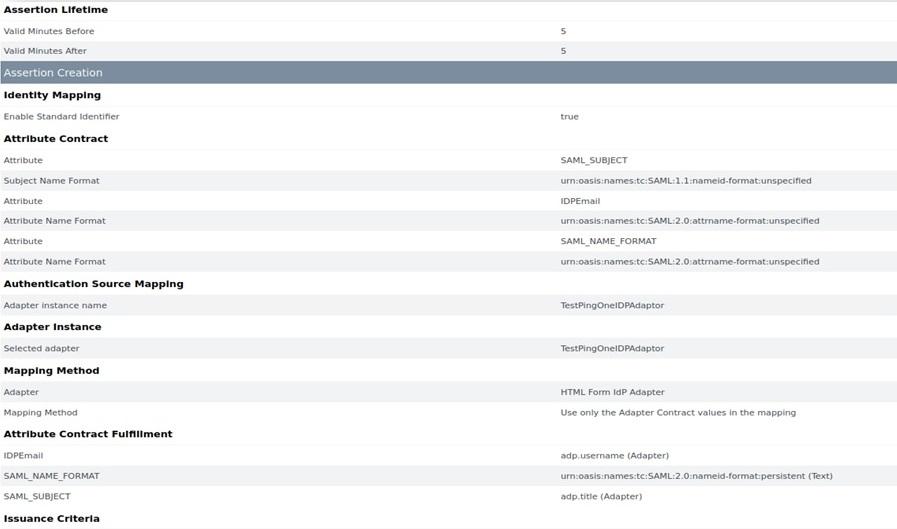
- In Assertion Creation>Authentication Source Mapping>Attribute Contract Fulfilment, extend the contract to add the following
Attribute
Description
SAML_SUBJECT
The value of this assertion attribute must be the same as the Azure AD user’s ImmutableID.
IDPEmail
Pass this attribute value in assertion as the O365 UPN value of the user.
SAML_NAME_FORMAT
Map this attribute value to this text: urn:oasis:names:tc:SAML:2.0:nameid-format: persistent
- In Protocol Settings>Allowable SAML Bindings, enable POST and REDIRECT
- In Protocol Settings>Signature Policy, select Always Sign Assertion
- In Credentials>Digital Signature Settings, select the PingFederate signing certificate
- If a signing certificate is not created, create one at PingFederate under Security>Signing
- Decryption keys and certificates
- Save the configuration
- Export the signing certificate
- Export and then open the metadata file and copy the values for:
- the entityID.
- SSO URL(https://<your value>/idp/SSO.saml2)
- SLO (https://<your value>/idp/SLO.saml2)
Example:


Steps to follow at Office 365
Run Windows PowerShell Command Prompt window (run as administrator) on any internet connected computer.
- Run command: Install-Module MSOnline
- Enter $cred = Get-Credential.
- Enter the username and password of your Office 365 administrator account in the pop-up
- Connect with MsolService.
- Connect-MsolService -Credential $cred
- List your domains.
- Get-MsolDomain
- Select the domain for which you would like to enable SSO.
- $dom = “<Your O365 domain>”
Set the PingFederate metadata details in the Office 365 configuration as below:
- Set the uri parameter to the PingFederate entityID value.
- $uri = “<Your entityID>”
- Set the url parameter to the PingFederate Location for SSO value.
- $url= “<Your Passive Log on Uri>”
- Set the logouturl parameter to the PingFederate Location for SLO value.
- $logouturl= “<Your Log Off Uri>”
- Open the downloaded signing certificate in Notepad, copy the encoded contents, and paste them into the command below to set the certificate parameter.
- $cert= “<Your certificate contents>”
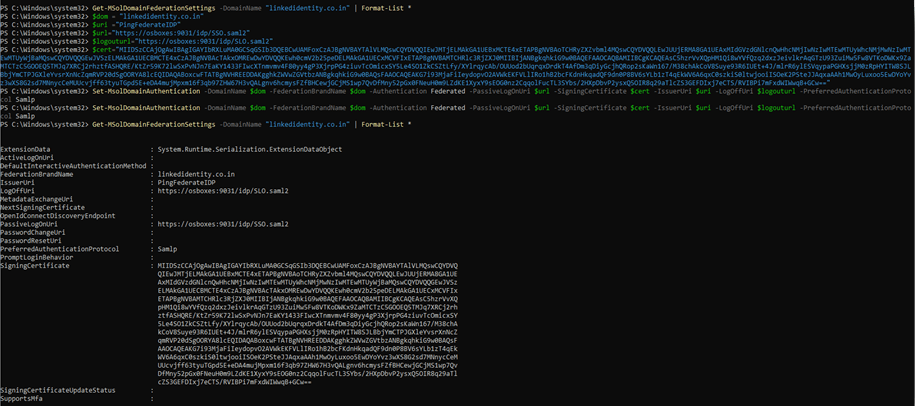
- Run the following command to setup SAML SSO for your domain
- Set-MsolDomainAuthentication -DomainName $dom -FederationBrandName $dom -Authentication Federated -PassiveLogOnUri $url -SigningCertificate $cert -IssuerUri $uri – LogOffUri $logouturl -PreferredAuthenticationProtocol Samlp
- Run the following command to see the completed SSO settings
- Get-MSolDomainFederationSettings -DomainName “<Your O365 domain>” | Format-List *
Example:
Test the configuration
Test the PingFederate IDP-initiated SSO integration:
- Go to the PingFederate SSO application endpoint for the Office 365 SP connection
- Example: https://osboxes:9031/idp/startSSO.ping?PartnerSpId=urn%3Afederation%3AMicrosoftOnline
- Complete PingFederate authentication
- You’re redirected to your Office 365 domain
Test the PingFederate SP-initiated SSO integration:
- Go to https://portal.office.com
- Enter your email address
- After you’re redirected to PingFederate, enter your PingFederate username and password
- You’re redirected back to Office 365