Cyber-attacks are demolishing businesses more than COVID-19 is. Don’t trust us?
See these two stats (there are tons of other stats):
- Up to 88% of UK companies have suffered cyber-attacks in the last 12 months (Source)
- One small business in the UK is successfully hacked every 19 seconds. (Source)

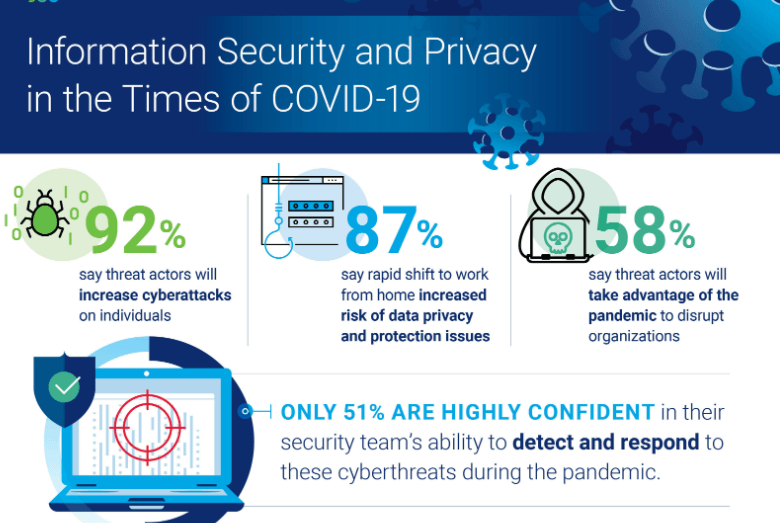
And this isn’t even the worst news. The situation is getting scarier in recent times due to the drastic increase in remote working (forced by the COVID-19 pandemic). More and more businesses are starting to adapt to a remote working environment. Service providers like doctors, teachers, law consultants, etc. are using remote tools to do business.
Result?
A Staggering number of data thefts, security trespasses, identity mismatches, etc. are reported across the globe.
What Has COVID-19 Done to Businesses?
Our mobility is hard-hit by the COVID-19 threat. Businesses have no option but to work remotely. Most business activities, including sales, are conducted online. We all prefer to work from home. As a business owner, you want to protect your employees. You don’t want to expose them (or yourself) to the deadly virus. Hence, you decide to connect with your employees through a remote set up. Sounds perfect.
Unfortunately, life-saving remote technologies are under threat of cyber-attacks.
Imagine leaving your house unlocked and sleeping at night. What would you see in the morning? That’s exactly the situation with unprotected online business communications. Still not serious?
Let’s see a few things that can happen:
Monetary loss – Theft of money and data. How hard it is to lose your hard-earned money. This is huge. Sometimes irreparable. An intruder in your network can easily swipe off the funds in seconds. You won’t even know it happened till you check the account statement.
Data loss – In business, data is gold. Customer data, business secrets, statistics, strategies, ideas… you name it. Priceless. Waking up one fine morning to know you have lost all your customer contact details is terrible, to say the least. Imagine losing the business plan, you and your team created for the new product launch next month.
Business loss – A sudden halt in business can cost you the reputation that you built over the years. System crashes are serious trouble. You don’t want to see your customers leave you because of a halt in your smoothly running business.
Unexpected Expenses – It’s not easy to get back the whole system up and running. Restoring crashed systems cost huge money and it might take days (if not weeks) to get them back in working condition.
Time loss – Your precious time is wasted in repairing and notifying the concerned parties about the deadly attack.
It is absolutely crucial to stay safe while leveraging remote working technologies to overcome the pandemic situation. This merging point is extremely important to succeed. This is where Identity & Access Management (IAM) system has become one of the most essential technologies for businesses of all sizes.
What Is IAM?
IAM refers to the tools and a set of rules used by IT departments to ensure only the authorised persons access the technical resources of the organisation. IAM systems are the technology tools to manage digital identities and their access rights to the software and hardware networks of the company. IAM systems not only manage people but also other kinds of identities like apps, programs, and IoT devices.
Simply put, IAM is a security system that guards the entry to your key cyber resources.
What are the business benefits of IAM?
The Control is in your hand
You control who gets access to which resources.
- Control employee access – control access to new joiners, mover and leavers – with automated rules
- Control customer access
- Control Partner / Vendor access
- Control 3rd party Contractor access
- Control access to Cloud Resources
All using a single Identity & Access Management system
Reduced IT costs
With the ability to automate many aspects of identity management, you’ll be able to cut down labour costs associated with keeping your business environment safe and secure.
Be regulatory compliant
Our IAM tools are designed in such a way that it adheres to all the rules and regulations regarding data governance and privacy management. IAM systems achieve this by centralizing control. As you hold the control, no employee can indulge in a data breach act.
Secure coupled with good UX
Modern-day employee & customer interaction happens across many platforms, both via the cloud and third-party apps. To enhance security and user experience, IAM also includes:
- Single sign-on (SSO) – Enables uses to securely log in to multiple applications with a single sign-on process.
- Multifactor authentication (MFA) – An additional layer of verification using OTP, facial ID, or fingerprint scans, devices etc…
The time to act is ‘NOW’
The world prefers to work from home. Partners / Customers prefer to ‘transact’ online. ‘Trust’ is based on ‘Online Identities’. This comes with risks. Manage these risks via an Identity & Access Management solution.