Ethical Hacking and Penetration Testing: Strengthening Cyber Defenses from the Inside

Cyber threats continue to evolve, with attackers employing increasingly sophisticated techniques to breach organizational defenses. In response, businesses must adopt proactive security measures to identify vulnerabilities before malicious actors can exploit them. Ethical hacking and penetration testing play a crucial role in this process, helping organizations uncover weaknesses and strengthen their cybersecurity posture. What is […]
Cybersecurity in the Metaverse: Protecting Users and Data in a Virtual World

The metaverse—a virtual, immersive digital environment where users interact, work, and socialize—is rapidly evolving. With major investments from tech giants like Meta, Microsoft, and Google, the metaverse is set to redefine digital experiences. However, with this new frontier comes a host of cybersecurity and privacy concerns that could leave individuals and businesses vulnerable to attacks, […]
The Impact of Quantum Computing on Cybersecurity: Preparing for the Post-Quantum Era

Quantum computing is no longer just a theoretical concept; it is evolving rapidly, with significant implications for cybersecurity. While quantum computers hold the promise of solving complex problems exponentially faster than classical computers, they also pose a major threat to current cryptographic standards. Organizations must prepare for the post-quantum era by understanding the risks, exploring […]
Cybersecurity for Critical Infrastructure: Strengthening Resilience Against Evolving Threats

Critical infrastructure sectors such as energy, healthcare, transportation, and finance form the backbone of modern society. These industries are vital to national security, economic stability, and public safety. However, as digital transformation accelerates, so does the risk of cyberattacks targeting these essential systems. Securing critical infrastructure has become an urgent priority, requiring a robust cybersecurity […]
Cloud Security Best Practices: A Comprehensive Guide

As organizations increasingly migrate to cloud environments, securing these infrastructures becomes a top priority. While cloud computing offers scalability, cost-effectiveness, and flexibility, it also introduces new security risks. Implementing robust cloud security measures is essential to protect sensitive data, manage access, and ensure regulatory compliance. This guide explores best practices for securing cloud environments effectively. […]
The Internet of Things (IoT) Security: Challenges and Strategies for Protection
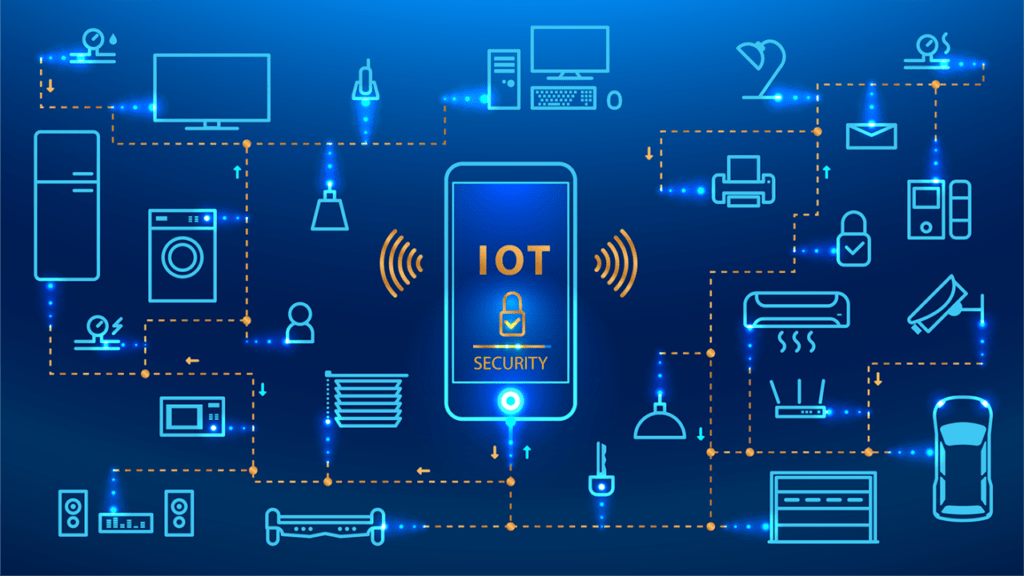
The Internet of Things (IoT) has revolutionized industries and everyday life, connecting billions of devices to enhance efficiency, convenience, and automation. However, this rapid proliferation of connected devices has also introduced significant security challenges. From smart home systems and industrial control networks to healthcare devices and autonomous vehicles, IoT devices present an expanded attack surface […]
Securing the Software Supply Chain: A Critical Imperative for Organizations

In today’s interconnected digital landscape, software supply chain security has become a top priority for organizations worldwide. Cybercriminals are increasingly targeting software vendors and third-party providers to infiltrate enterprise systems, compromise sensitive data, and launch large-scale attacks. The growing complexity of supply chains, coupled with the increasing reliance on third-party software, makes it essential for […]
The Human Factor in Cybersecurity: Building a Security-Conscious Culture

Cybersecurity is often perceived as a purely technical domain, with firewalls, encryption, and threat intelligence tools taking center stage. However, even the most advanced security technologies are only as strong as the people who use them. Employees are the first and last line of defense against cyber threats. One weak link—be it a moment of […]
. The Role of AI in Cybersecurity: Enhancing Threat Detection and Response

As cyber threats grow more sophisticated, traditional security measures struggle to keep up. Cybercriminals continuously evolve their tactics, making it imperative for organizations to adopt advanced defense mechanisms. This is where Artificial Intelligence (AI) and Machine Learning (ML) step in, transforming cybersecurity by enabling proactive threat detection, intelligent automation, and faster incident response. How AI […]
Implementing Multi-Factor Authentication (MFA): Best Practices and Benefits

In today’s cybersecurity landscape, passwords alone are no longer sufficient to protect sensitive information. Cybercriminals constantly exploit weak or stolen passwords, making Multi-Factor Authentication (MFA) an essential security measure for businesses and individuals alike. MFA enhances security by requiring users to verify their identity using multiple authentication factors, significantly reducing the risk of unauthorized access. […]